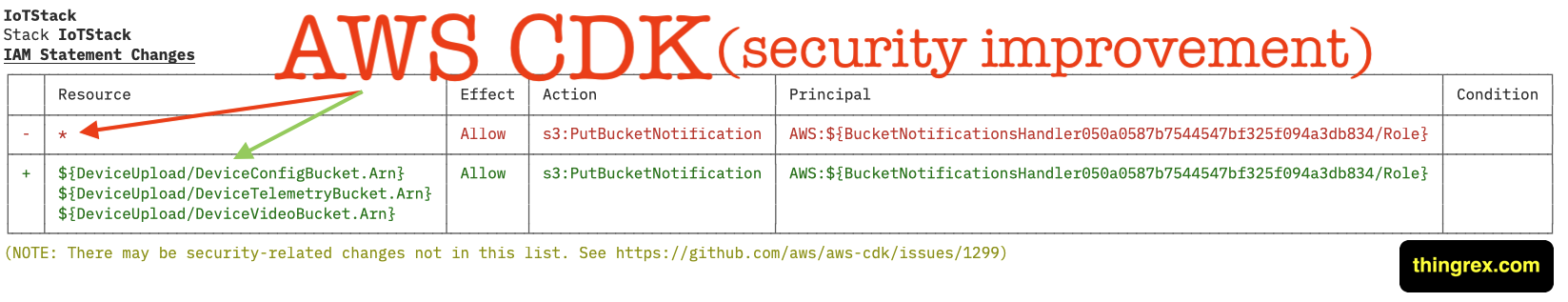
In a properly managed environment, the delta between your Infrastructure-as-Code (IaC) and your actual cloud environment should be zero.
When your monitoring solution triggers a drift alert (you do have automated drift detection, right?), it typically points to one of two scenarios:
🔴 Scenario A (The Rogue Operator): Someone bypassed the governance and manually modified resources in the AWS Console. This is problematic as manual actions are error-prone and hard to track (and even harder to revert).
🟢 Scenario B (The Platform Evolution): The underlying provider updated the baseline security posture.
Fortunately, this time we are facing Scenario B.
AWS rolled out a security improvement to CDK-managed resources, triggering an “unexpected” drift notification. This wasn’t a developer’s mistake; it was the platform tightening the Principle of Least Privilege, closing minor risks caused by too broad permissions in legacy deployments.
The Strategic Lesson:
If you weren’t monitoring drift, you wouldn’t know the difference between a security patch and a security breach.
Reliability requires Governance, not just code. You must know exactly what changed, who changed it, and why.
Is your engineering reality drifting away from your business strategy?
👉 Contact me to discuss an Architecture & Strategy Review.
