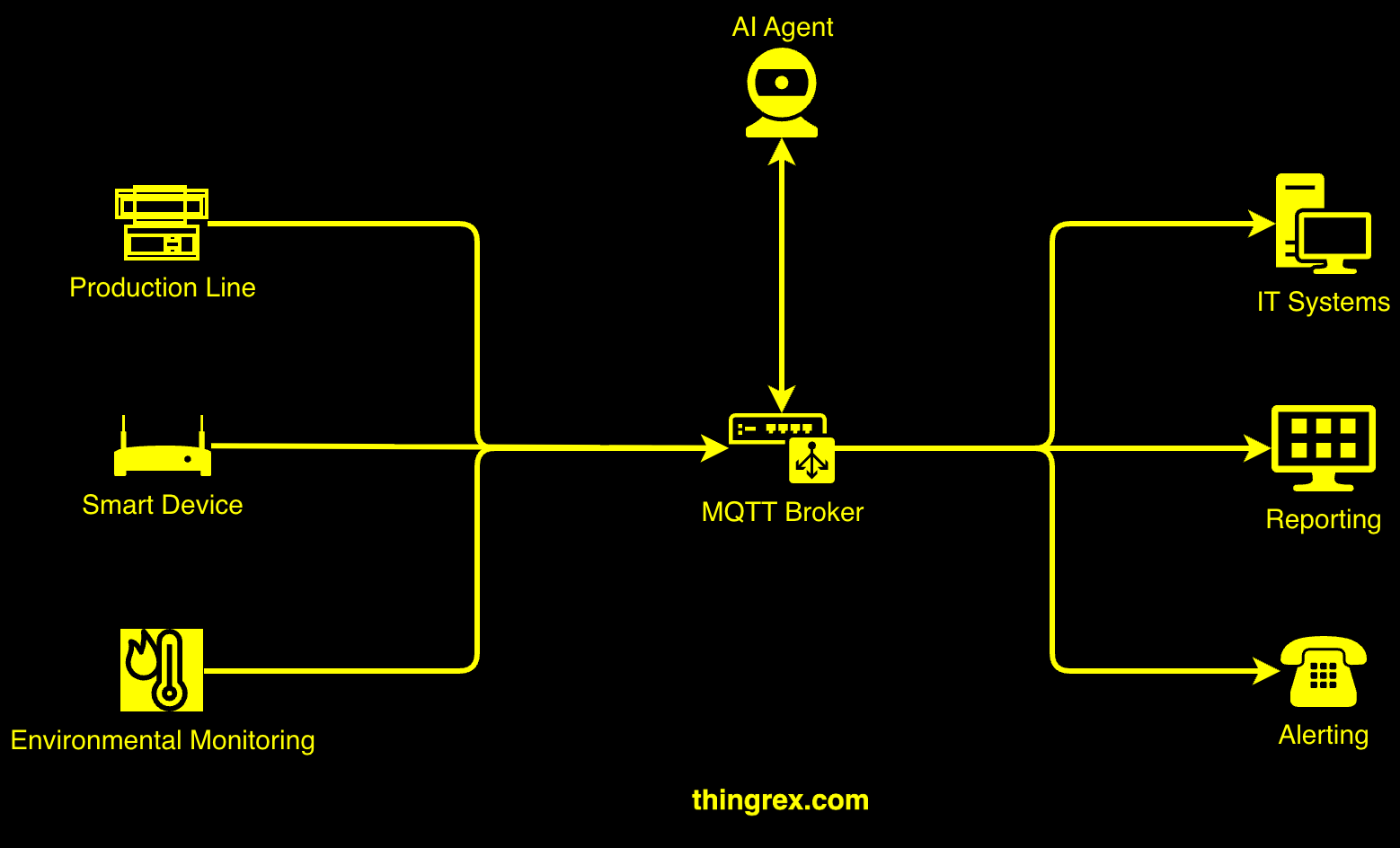
Anomaly detection that understands context
I have been experimenting with various AI agentic workflows over the past months, testing different architectural patterns and seeing where they deliver real value. Suddenly, I realized this technology is a perfect fit for IoT workloads that use MQTT (the primary protocol for managing devices).
I have worked with MQTT for years, but I had not connected it to AI agents until recently. MQTT’s pub/sub architecture creates something unique: a continuous data stream that agents can subscribe to without impacting the environment.