Overview
Some web applications are available only from the server they are running. In other words, they listen only for incoming connections from the local host.
This means that even the administrator can not access them using a web browser running on another computer.
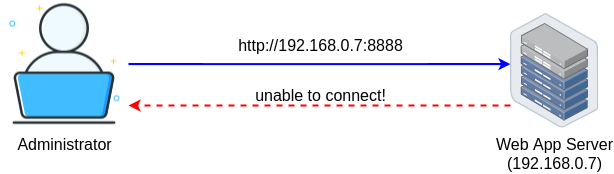
Those are typically very important web applications with restricted access. One example of this kind of application is a web control panel running on the factory floor equipment.
To access those applications (i.e. for debug or maintenance), you can use SSH port forwarding.
IMPORTANT: to use the SSH port forwarding, you need the SSH access to the server hosting web application.
To explain this concept, I will use my life-monitoring project.
Life-monitoring environment
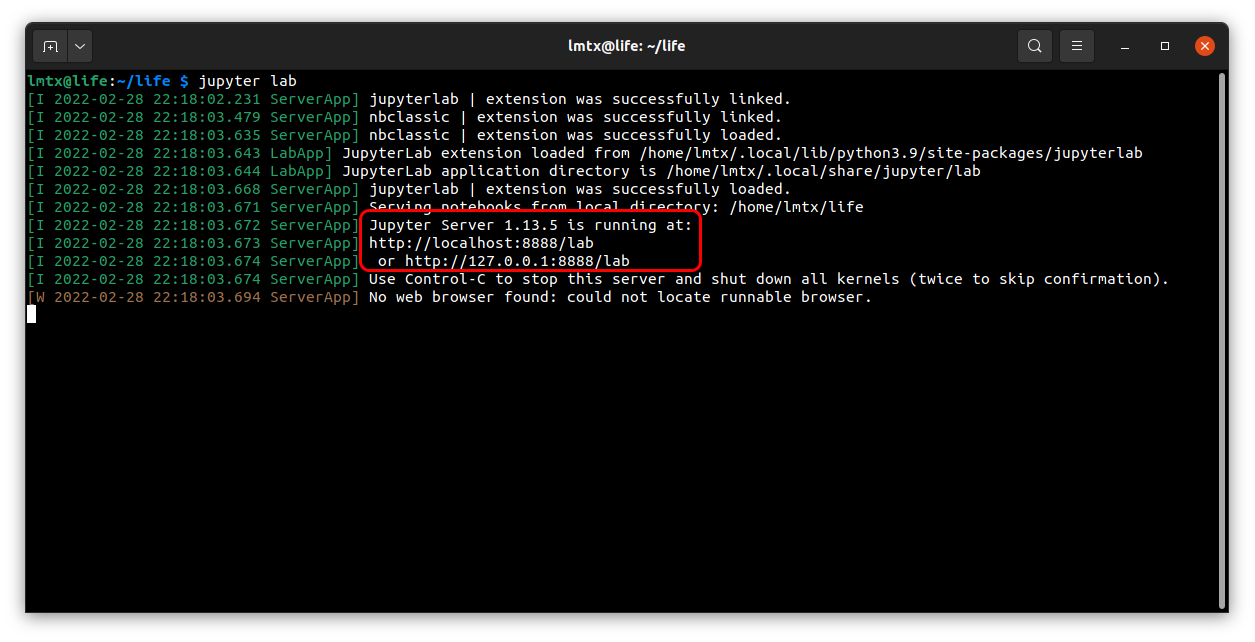
My very important web application is a Jupyter Lab server running at the Raspberry PI.
This web application can execute Python scripts and provides terminal access - very good reasons to keep it secure!
I will use the curl command for web access testing. The curl command “emulates” web browser and presents responses from the server.
Let’s try to access Jupyter Lab directly from my laptop:
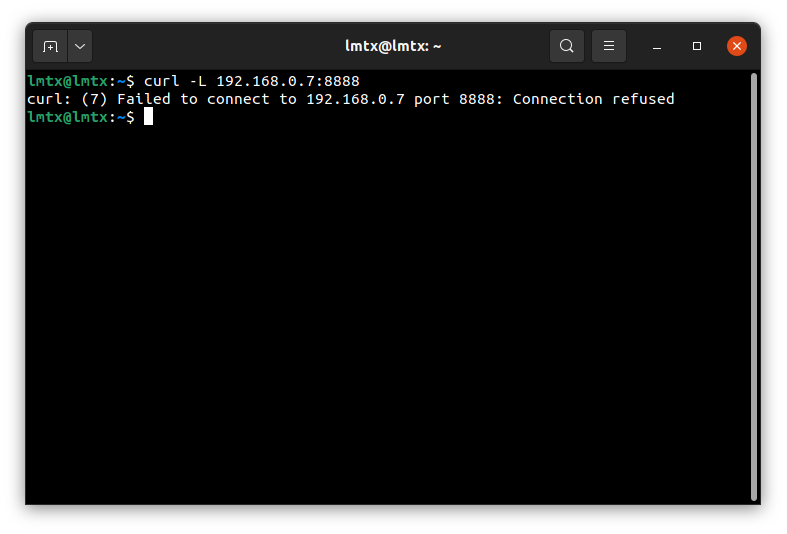
So maybe we should try connecting to the 127.0.0.1:8888 as the output from Jupyter Lab suggested?
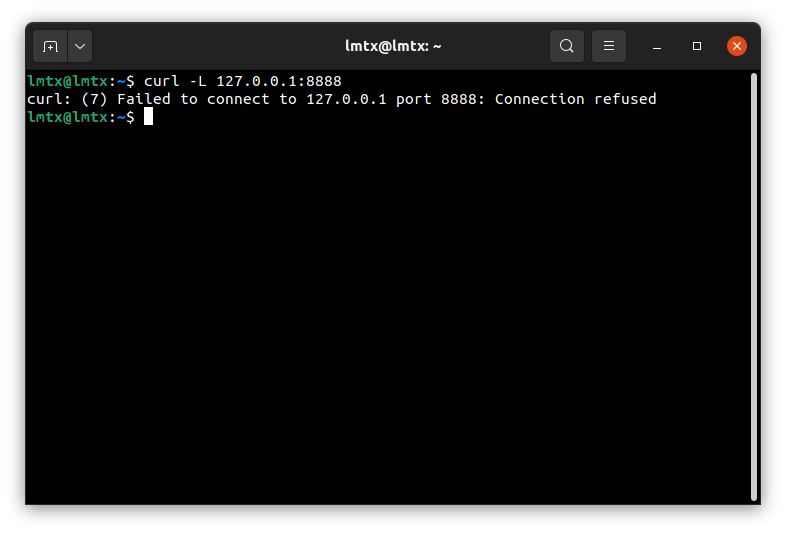
That was a very naive try, the 127.0.0.1 points to my laptop (that is the localhost), not to the Raspberry PI.
We proved that we can not access the Jupyter Lab in a “typical way”.
SSH port forwarding
The SSH port forwarding works as follows:
|
|
SSH man description:
|
|
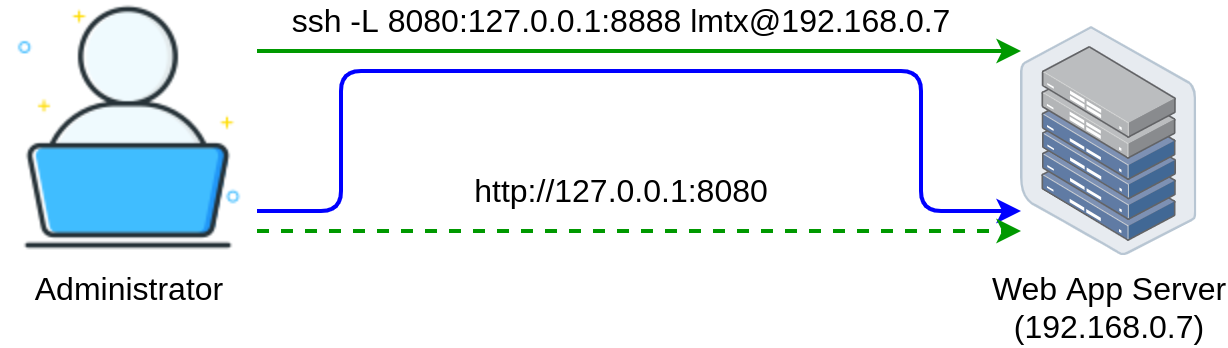
It looks something like this:
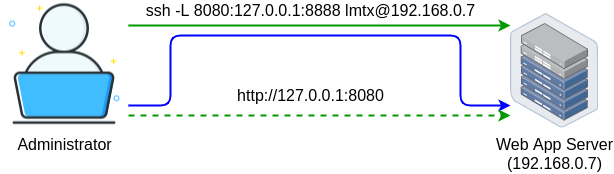
Let me break this down:
8080- is the local port (I used the8080to demonstrate that the local port on my laptop can be different from the target port used by the remote application, you can use any Ephemeral port)127.0.0.1:8888- is the destination host and port (127.0.0.1is the localhost on Raspberry PI, not my laptop!)lmtx@192.168.0.7- is the user @ IP address of the SSH server used for port forwarding
Let’s establish port forwarding on my laptop:
|
|
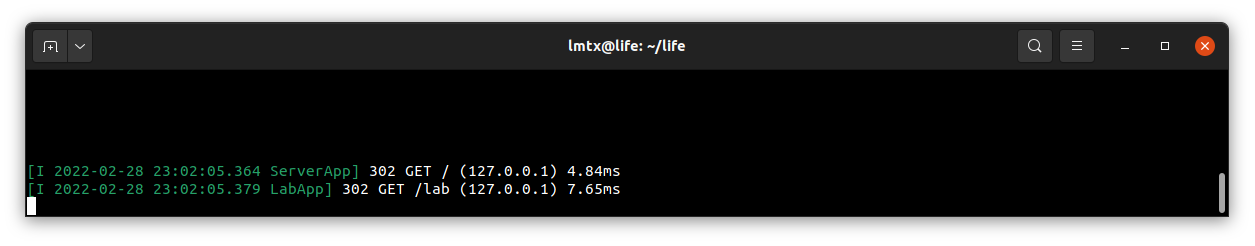
And test our connection to the secure web application:
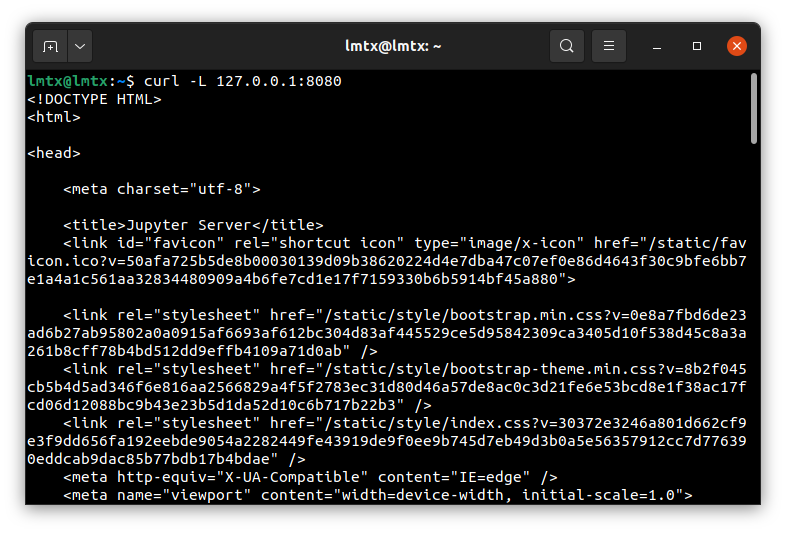
Jupyter Lab running at the Raspberry PI received this connection:
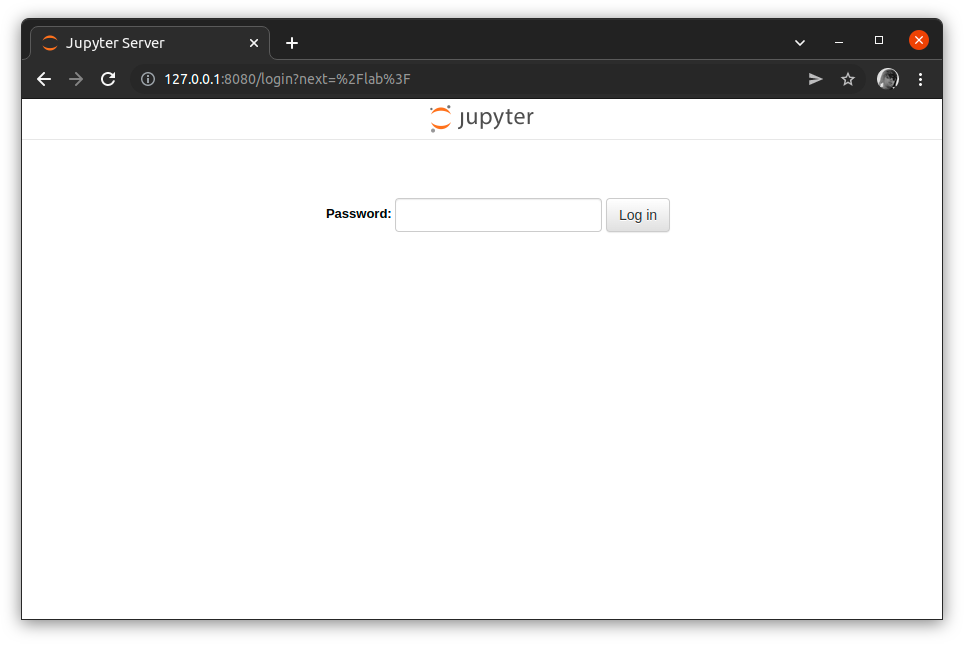
Finally, let’s connect to the Jupyter Lab running at the Raspberry PI using a web browser:
Conclusion
SSH port forwarding is not strictly an “IoT skill”, but this technique is very useful (also for IoT consultants).
Port forwarding can be used not only to access web applications. You can use this approach to access any isolated applications (like databases accepting connections exclusively form the localhost).