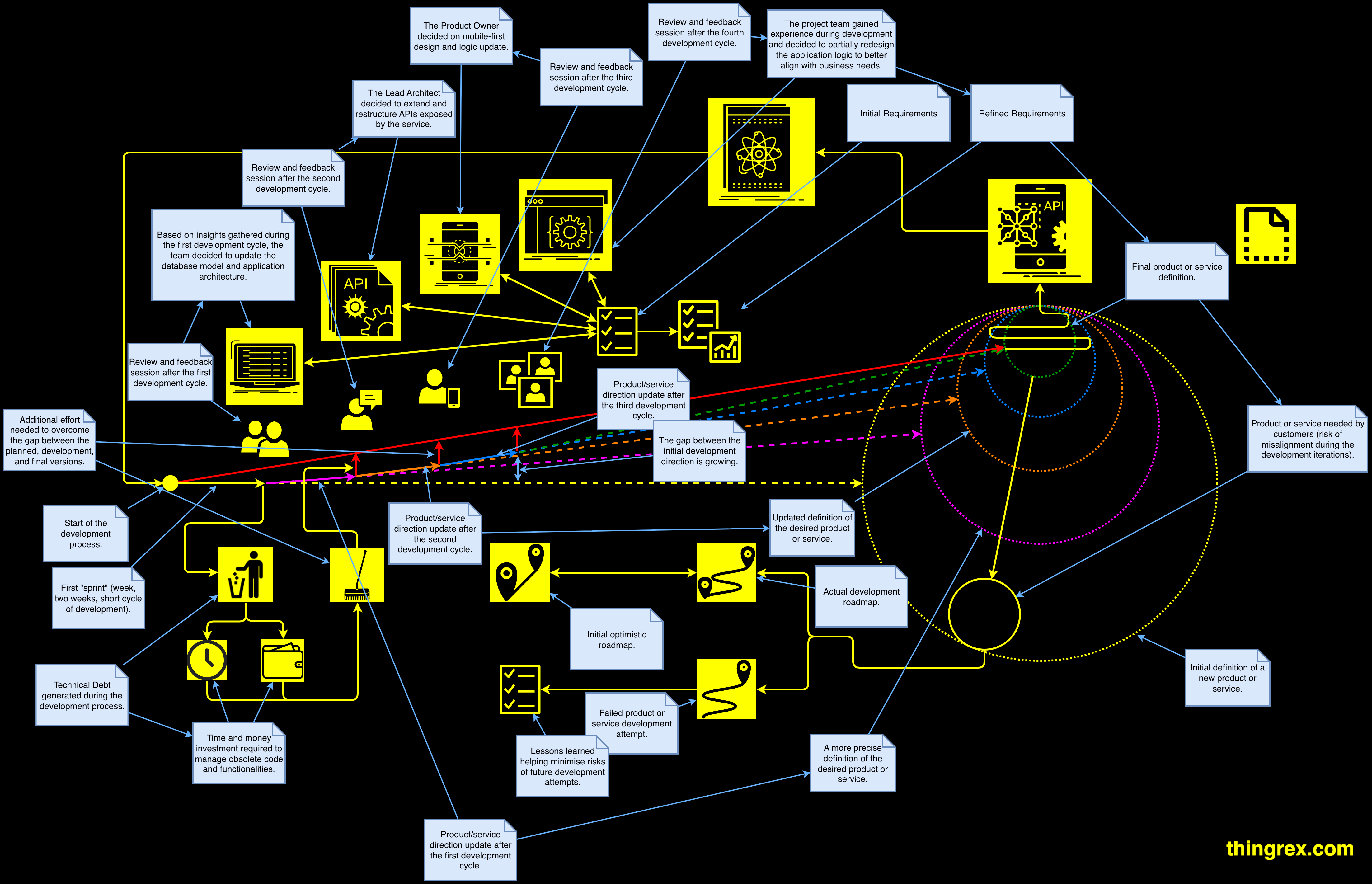
Iteration isn't the problem. Uncontrolled iteration is.
This diagram illustrates a pattern I see in hardware-enabled SaaS initiatives. You start with initial requirements and an (optimistic) roadmap.
Then reality shows up:
❌ The field data disagrees.
❌ Ops workflows change.
❌ Customers/stakeholders ask for “just one more adjustment."
❌ The team constantly refactors APIs, reshapes the data model, rewrites logic, etc.
Each iteration does improve the product…
…but it also creates iterative debt: leftover code paths, half-migrated schemas, compatibility layers, rushed fixes, duplicated logic.