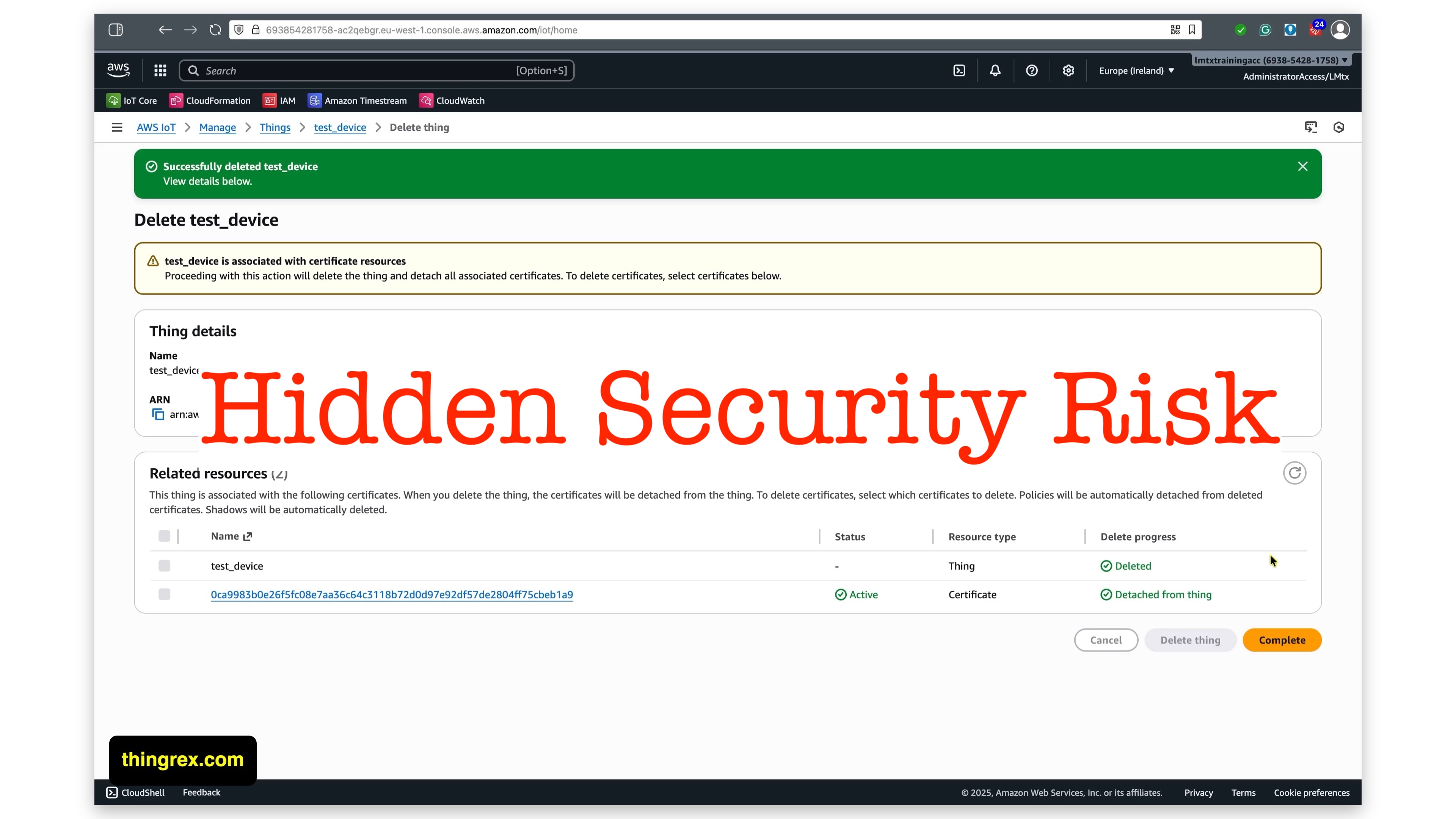
You just finished testing your IoT device. Time to clean up. You navigate to AWS IoT Console, find your Thing under Manage → All devices → Things, and hit delete.
Done, right?
Wrong.
Here’s the thing: deleting an IoT Thing only removes the logical representation of your device. The certificate (your device’s proof of identity) remains active with policies attached.
That’s a security hole.
What Actually Happens
When you delete a Thing in the AWS console, you’ll see a helpful summary of related resources. The new console interface even shows you the certificate. But here’s what it doesn’t tell you clearly enough:
An active certificate with attached policies can still potentially enable access to your AWS environment.
If someone has the private key (and they might, if this was a test device), they can use that certificate to communicate with your AWS infrastructure. Your Thing is gone, but the vulnerability remains.
The Proper Cleanup Process
- Delete the Thing (the logical device representation)
- Navigate to the certificate via the related resources link
- Go to Actions → Delete
- Confirm certificate deletion
Only after both steps are complete is your device truly disconnected.
The Bottom Line
The AWS IoT console has improved, but it’s still easy to leave security gaps during cleanup. Every active certificate is a potential attack vector.
What you should remember: Deleting a Thing is only half the job. Always delete the certificate.
Based on my professional experience, this is one of the most common oversights in IoT projects - especially during the testing phase when teams are moving fast and cleaning up quickly.
Need help securing your IoT infrastructure? Let me know if your organization requires expert guidance on AWS IoT security and cost optimization.
