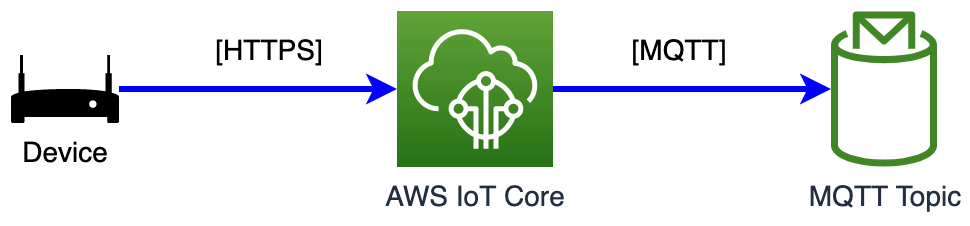
Introduction
During the Internet of Things engagements, we need to adapt our solution to the capabilities offered by existing hardware and/or firmware.
In some cases, our devices might not be able to use “fancy” MQTT clients. Is there a way to connect those devices to the AWS IoT Core?
One of the possible options is to use the HTTPS protocol to publish messages from those devices to AWS.
Limitations of the HTTPS protocol
Before I present how can we send messages to AWS IoT Core using the HTTPS protocol, I want to underline some important limitations of this approach:
- this method is “Publish only” - devices can send messages using HTTPS to the IoT Core, but they can not receive any messages from IoT Core,
clientIdis not supported andiot:Connection.Thing.ThingNameIoT Policy variable is not available for HTTPS connections - this impacts our IoT Policies and makes them hard to manage. If you need a quick introduction to the IoT Core Policy Variables, I described this topic in my previous post.
HTTPS Publish
Before publishing, we need to obtain the AWS IoT device data endpoint (to know the target of our messages):
|
|
I will use a simple curl command to send a message to AWS IoT Core using the HTTPS protocol and device credentials:
|
|
I will use the MQTT test client to verify that our message was received by the AWS IoT Core:
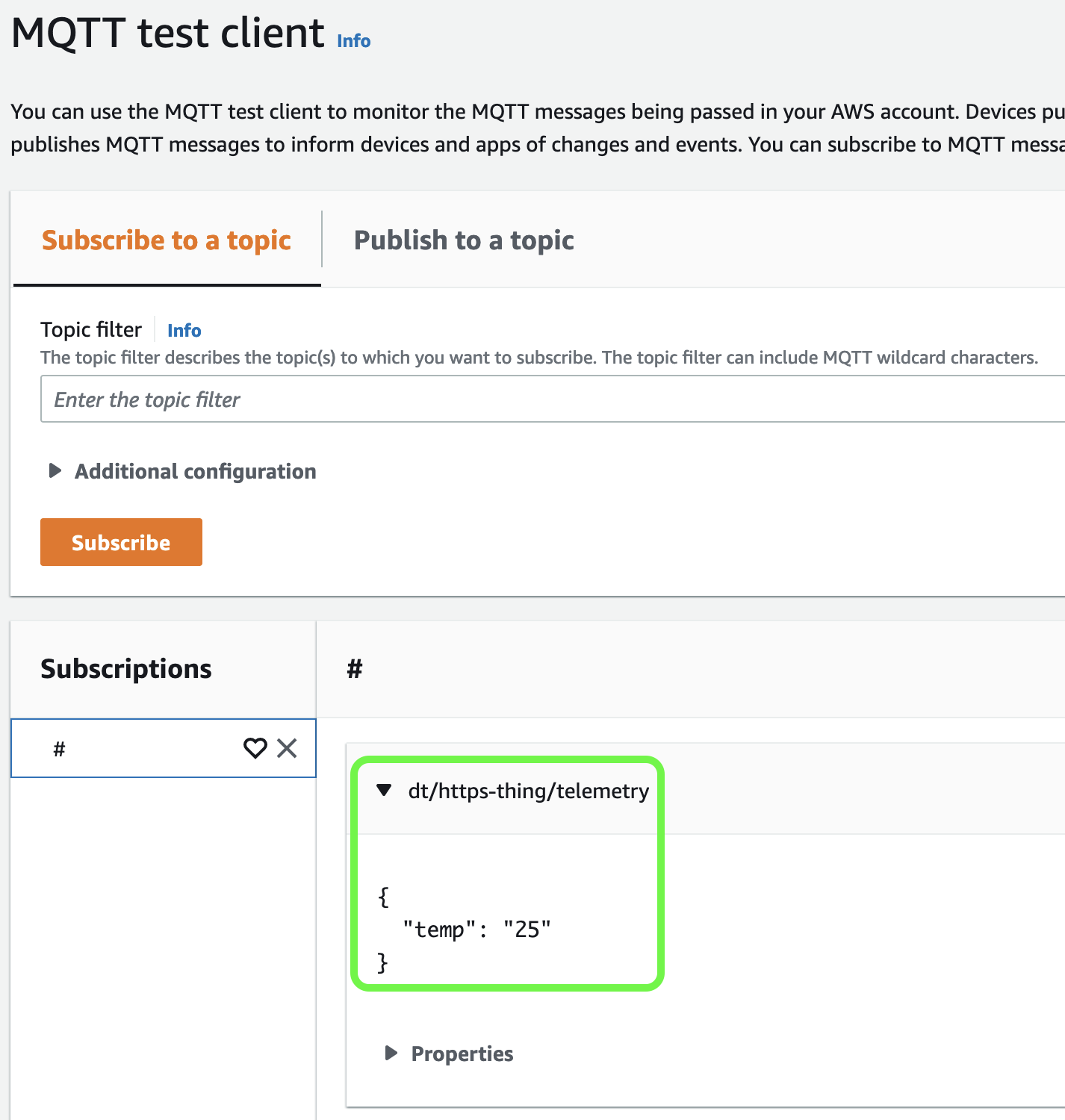
At this stage, we can process this message the same way we are processing “typical” MQTT messages.
What if we try to send a message to the Topic that is not allowed for our device?
|
|
Instead of "message":"OK" we received "message":null.
HTTPS Subscribe
There is no way to subscribe using the HTTPS protocol - in other words, our devices are not able to receive any data from the AWS IoT Core.
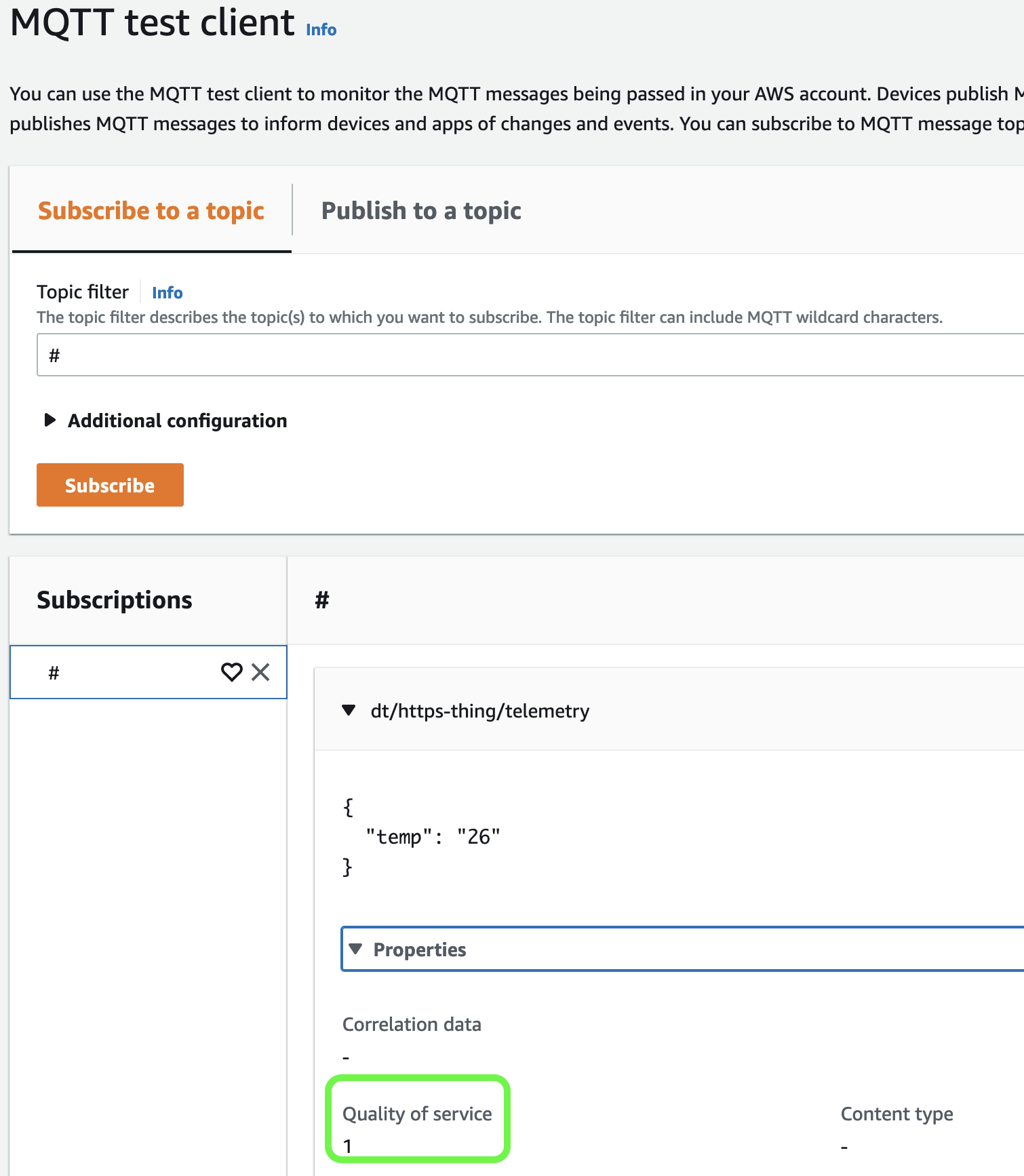
QoS
To define the MQTT QoS (Quality of Service) when sending messages using HTTPS add the ?qos= at the end of the URL. If you are not sure what the QoS is, please check my MQTT cheat sheet.
IMPORTANT: Please remember that AWS IoT Core currently supports only QoS 0 and 1 - docs.
|
|
ClientId is NOT supported
Why that is important? Because typically we use the clientId to write flexible yet restrictive IoT Policies.
The Thing Name is obtained from the client ID in the MQTT Connect message sent when a Thing connects to AWS IoT Core - we read this value from the iot:Connection.Thing.ThingName Thing Policy Variable when we use the MQTT protocol.
If this topic is not clear to you please check my previous post.
Unfortunately, the clientId is not set for messages sent using HTTPS.
To verify this, let’s create the following IoT Rule:
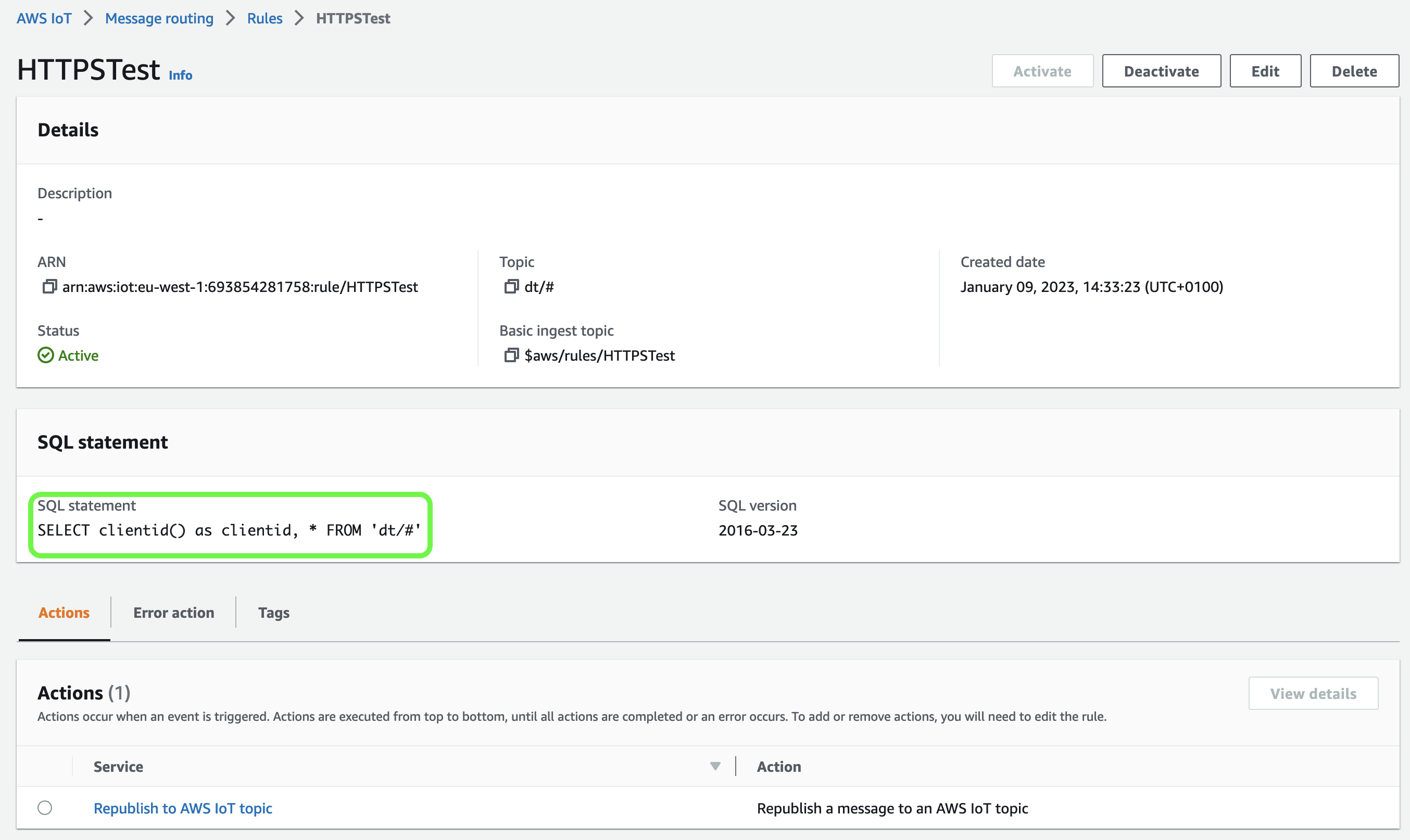
In the SQL statement, we use the clientid() function, which returns the client ID or N/A if that value was not set.
Let’s publish the following message:
|
|
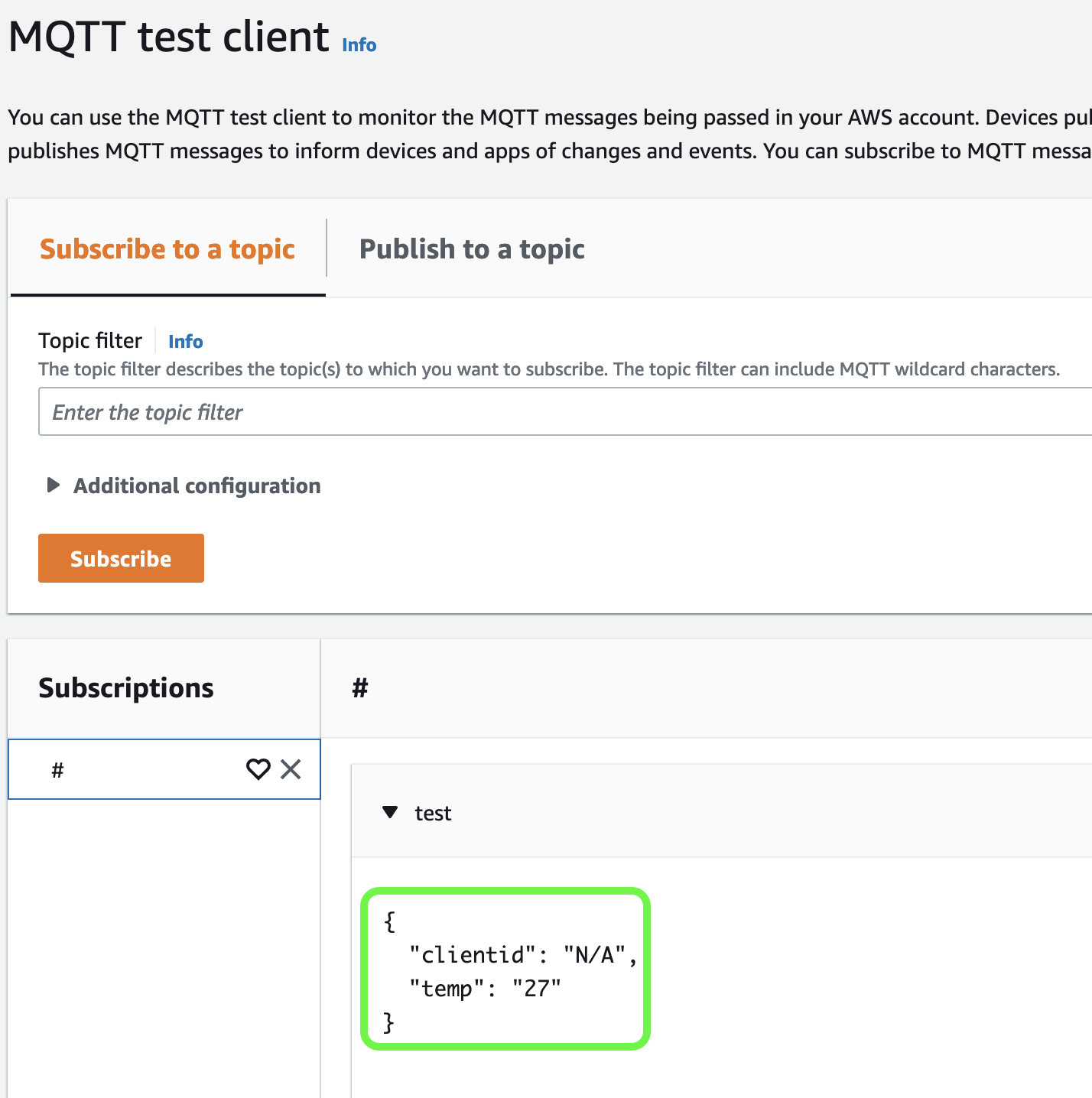
To compare, we can make a quick test using the MQTT protocol:
|
|
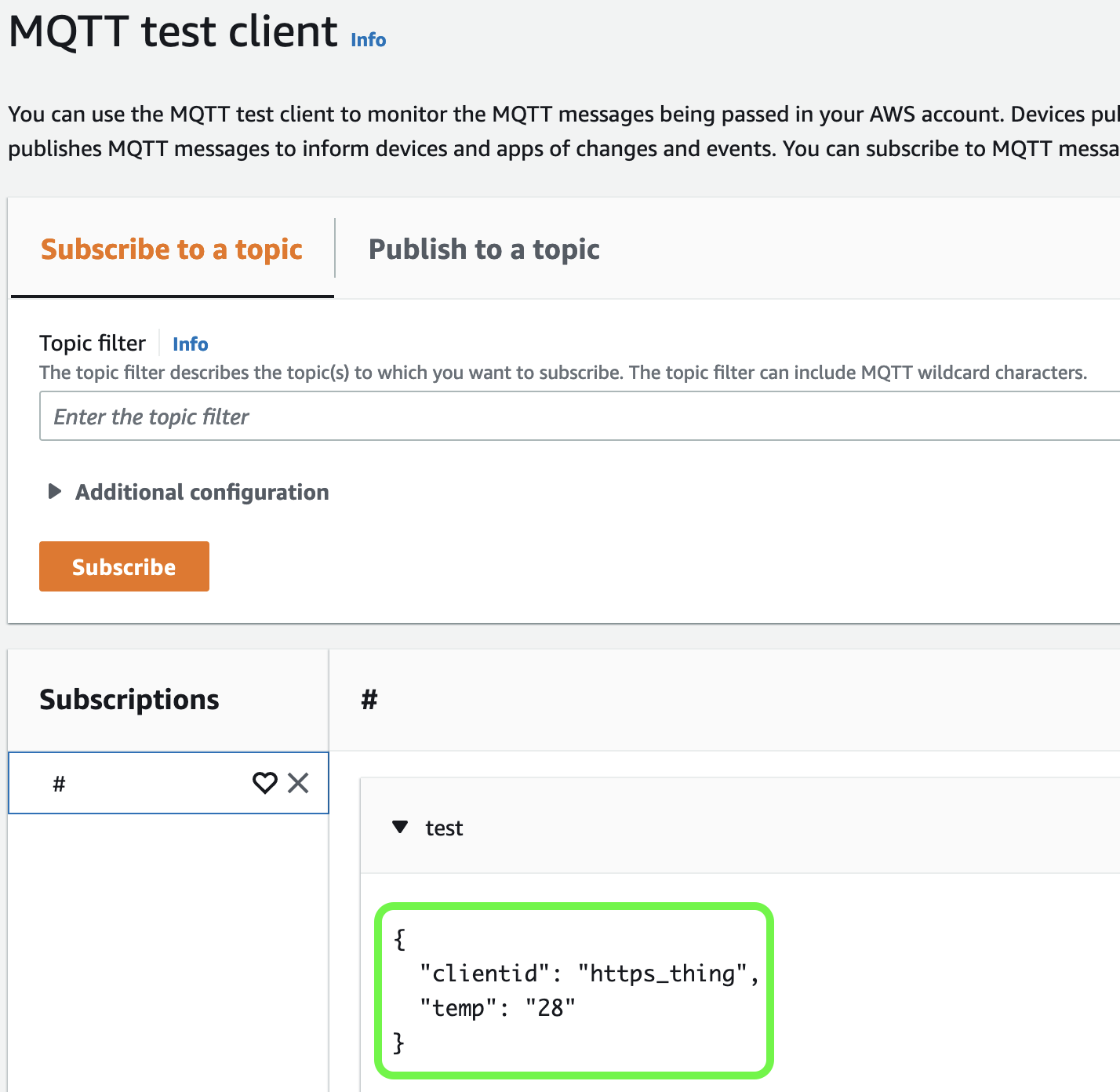
Summary
This concludes my short overview of sending messages to the AWS IoT Core using the HTTPS protocol.
If you decide to use this approach, please design AWS IoT Policies with care. Since the clientId is not supported in communication using HTTPS, you need to hardcode your policies which will make them hard to manage at scale.

