
Introduction
Today I will explain how connected devices can establish trust with the AWS IoT Core. To trust someone, we need to confirm their identity. The same is true in the ecosystem of connected devices.
AWS IoT Core exposes an MQTT Broker so devices can establish the MQTT connectivity.
What if some villain actor creates an MQTT Broker and tries to mislead devices? Is there a way to verify the real identity of the exposed endpoint?
Short answer: Yes, devices can verify the identity of the exposed endpoint and establish a connection only after they confirm that they are communicating with the AWS IoT Core.
Long answer: This is a very technical post. I describe how the verification process works and explain the usage of X.509 Certificates.
Step one - AWS IoT Core endpoint types
We use the AWS IoT data endpoint for communication between connected devices and AWS. This endpoint enables secure, bi-directional communication for devices.
There are two data endpoint types: iot:Data and iot:Data-ATS.
The iot:Data is a legacy endpoint, so I recommend using the iot:Data-ATS (ATS stands for Amazon Trust Services).
How can we obtain the AWS IoT data endpoint?
AWS IoT data endpoint is account and region-specific. We can obtain it using AWS CLI:
|
|
Response:
|
|
We know the endpoint, but how can we verify its identity?
X.509 Certificates exposed by the AWS IoT data endpoint
To establish trust, we need to confirm the identity of the obtained endpoint.
We can check X.509 Certificates exposed by that endpoint using the following command:
|
|
Truncated response:
|
|
Let’s check the Certificate chain:
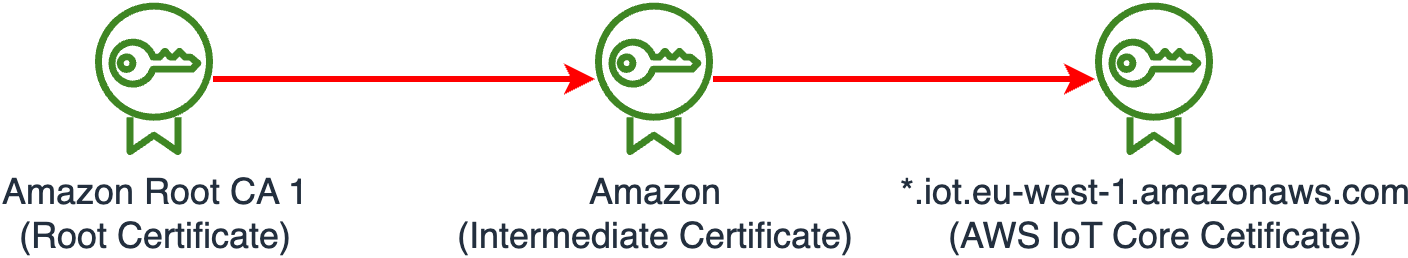
CN = *.iot.eu-west-1.amazonaws.com is the Common Name (CN) of the AWS IoT Core certificate.
CN = Amazon is an Intermediate Cetificate.
CN = Amazon Root CA 1 is the Root Certificate.
The chain looks as follows:
We can save those certificates using the following command:
|
|
Let’s review the certificate exposed by the AWS IoT Core:
|
|
Response:
|
|
The Common Name (CN) of the issuer equals “Amazon”. We can review that intermediate certificate:
|
|
|
|
The intermediate certificate was signed by the Amazon Root CA 1 certificate.
The Amazon Root CA certificate
Now we need to obtain the Amazon Root CA 1 certificate. That certificate is publicly shared by Amazon, we can download it using the following command:
|
|
Finally, we need to verify if that certificate was used to sign the chain of certificates exposed by the AWS IoT Core.
|
|
Response:
|
|
A quick reminder:
AmazonRootCA1.pem- the certificate we downloaded from the www.amazontrust.comcert_2.pem- the intermediate certificatecert_1.pem- the certificate exposed by the AWS IoT Core during connecting
We obtained the AmazonRootCA1 certificate from a trusted source and used it to verify certificates from a (potentially) untrusted endpoint.
That is why we need to put the AmazonRootCA1 certificate on every device connected to AWS IoT Core - devices use this certificate to establish trust during the connecting setup with the AWS IoT Core.
Summary
I know that was a deep-dive technical post, but I wanted to explain the very important topic of trust in the IoT system. I hope this was interesting for you.

